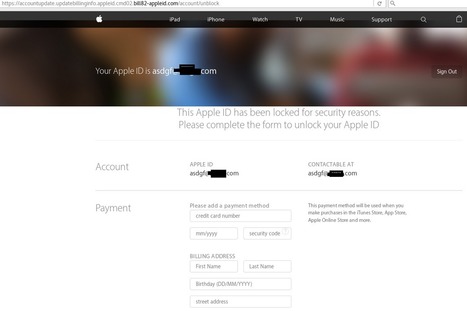
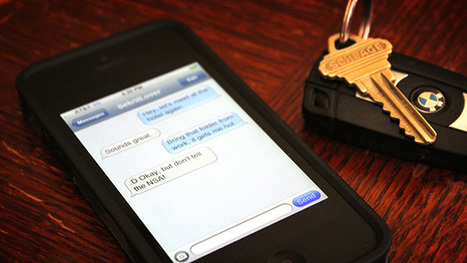
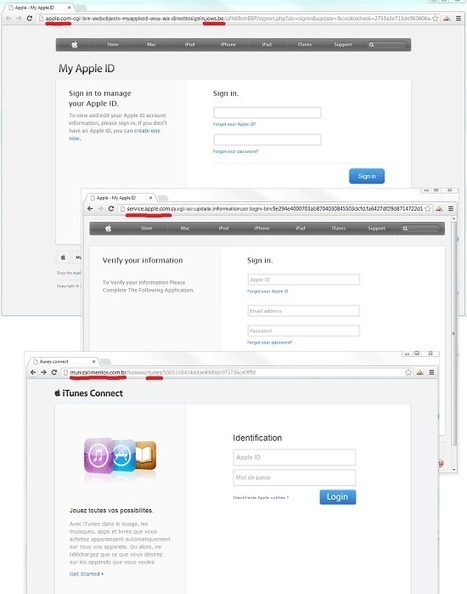
Mit gefälschten E-Mails und Webseiten wollen Kriminelle Zugangsdaten von Apple-Nutzern erschleichen. Die Phishing-Seiten setzen auf "gute Optik" und geben sich durch https-Verschlüsselung einen seriösen Anschein, warnt die Polizei Niedersachsen.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security



 Your new post is loading...
Your new post is loading...





Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security